#
ELLIO: Threat List MAX for ntopng
#
Introduction
You can get a visibility into your network traffic with ntopng. With ELLIO: Feed for ntopng, you can enrich your ntopng with the information about the threats that are hitting your network perimeter.
#
Requirements
#
ntopng
If you are on the dev branch of ntopng, you can use ELLIO: Threat List MAX out of the box -
If you are on the stable branch of ntopng, first add ELLIO: Threat List MAX using
Stable release of ntopng with ELLIO: Feed out of the box will be release in summer 2024.
#
ELLIO: Threat List MAX
You will need ELLIO: Threat List MAX. Sign-up for ELLIO: Threat List MAX for ntopng trial - you will receive the link to your ELLIO: Threat List MAX in the email after the sign-up.
#
Setup
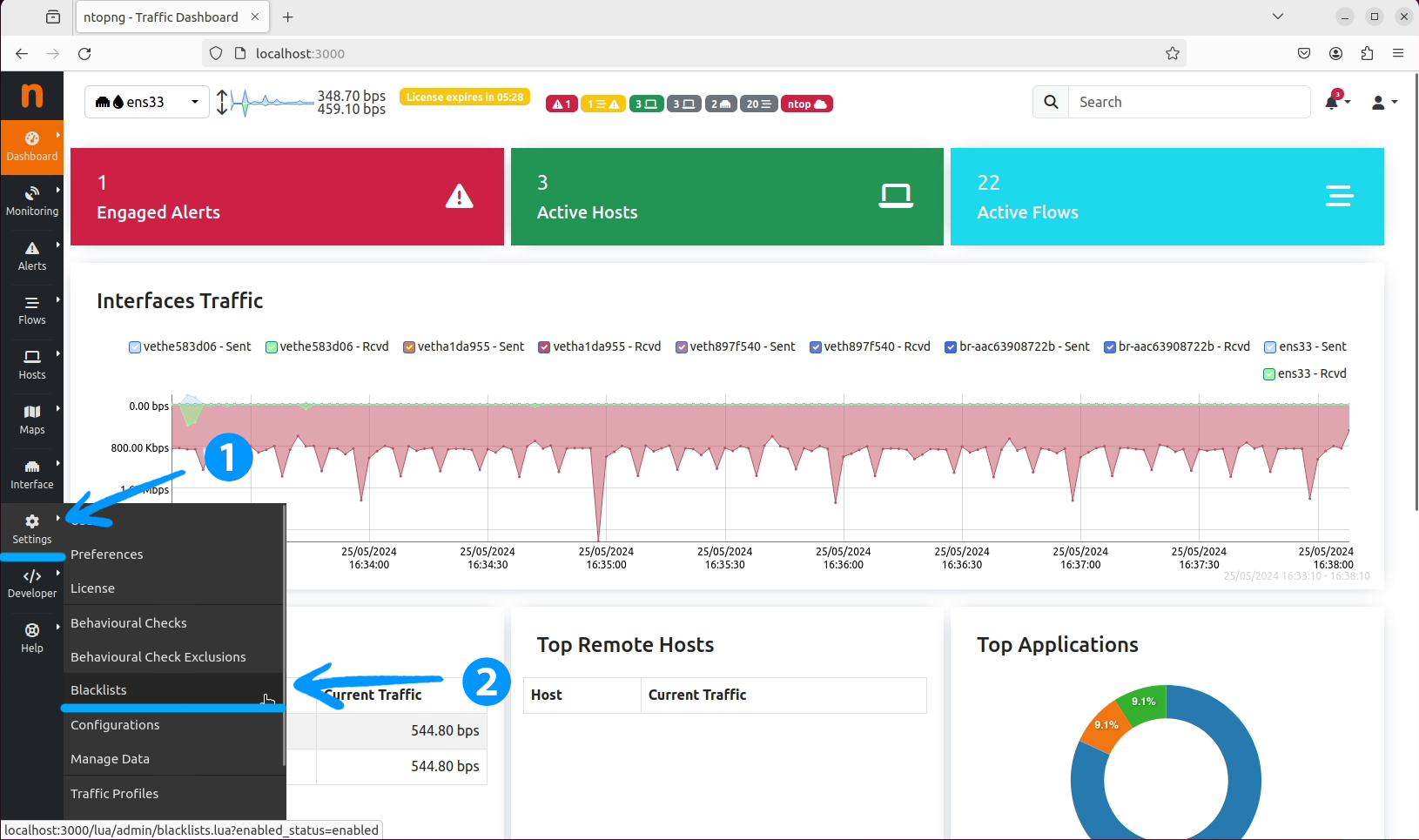
Settings tab and then to the Blacklists section.
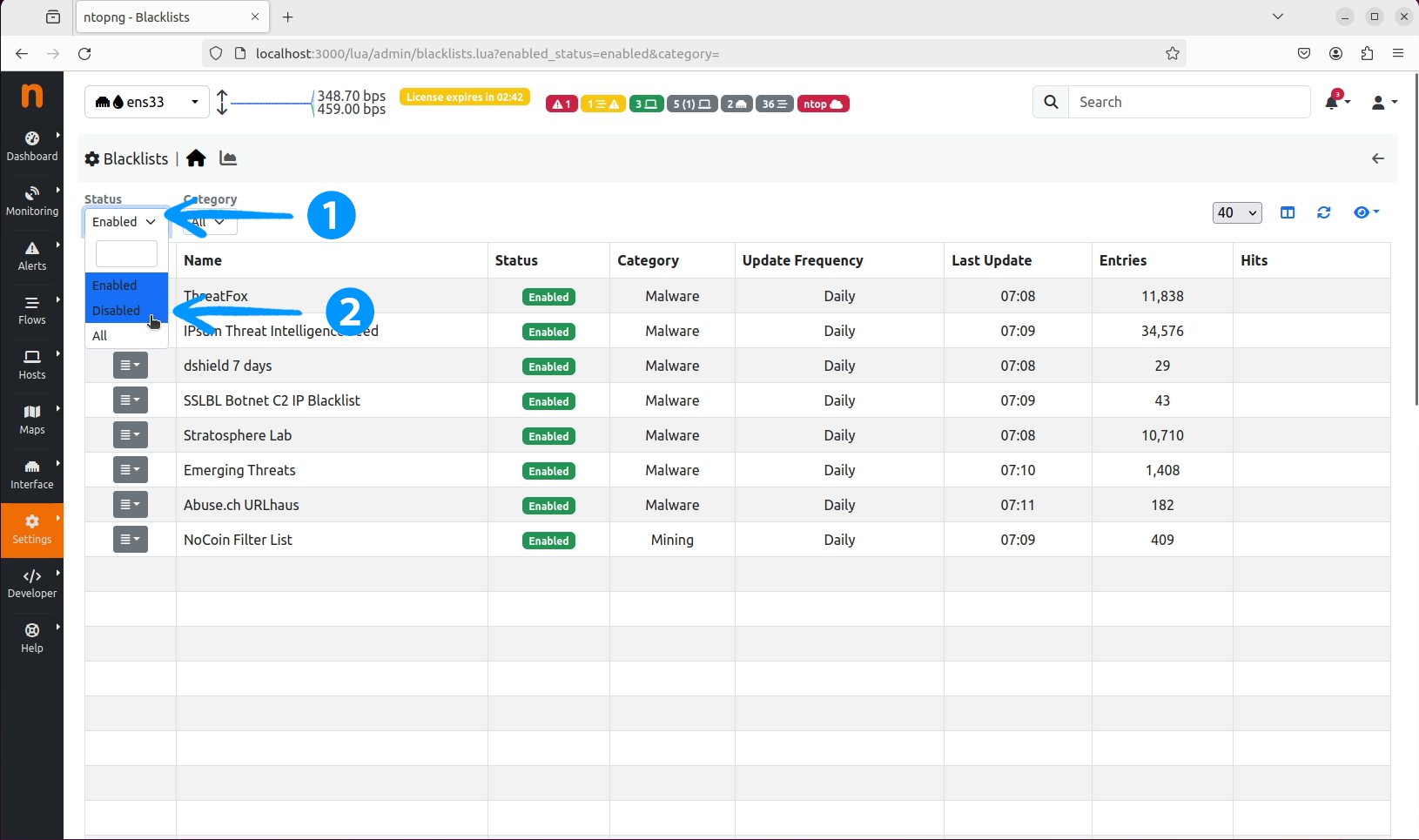
Blacklists section, click on the Status dropdown and select Disabled.
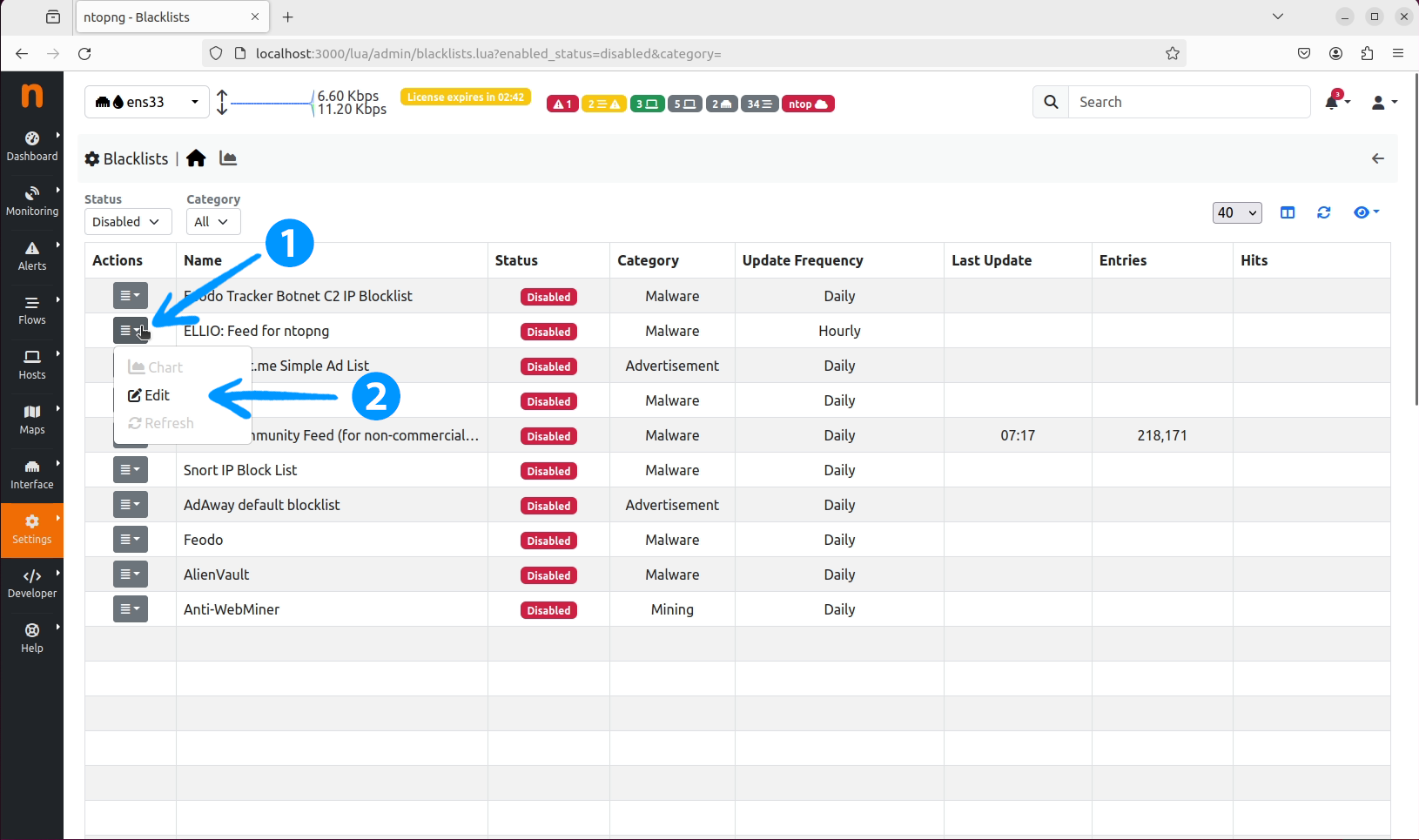
ELLIO: Threat List MAX for ntopng and click on the action button on the left side of the row. Select Edit from the dropdown.
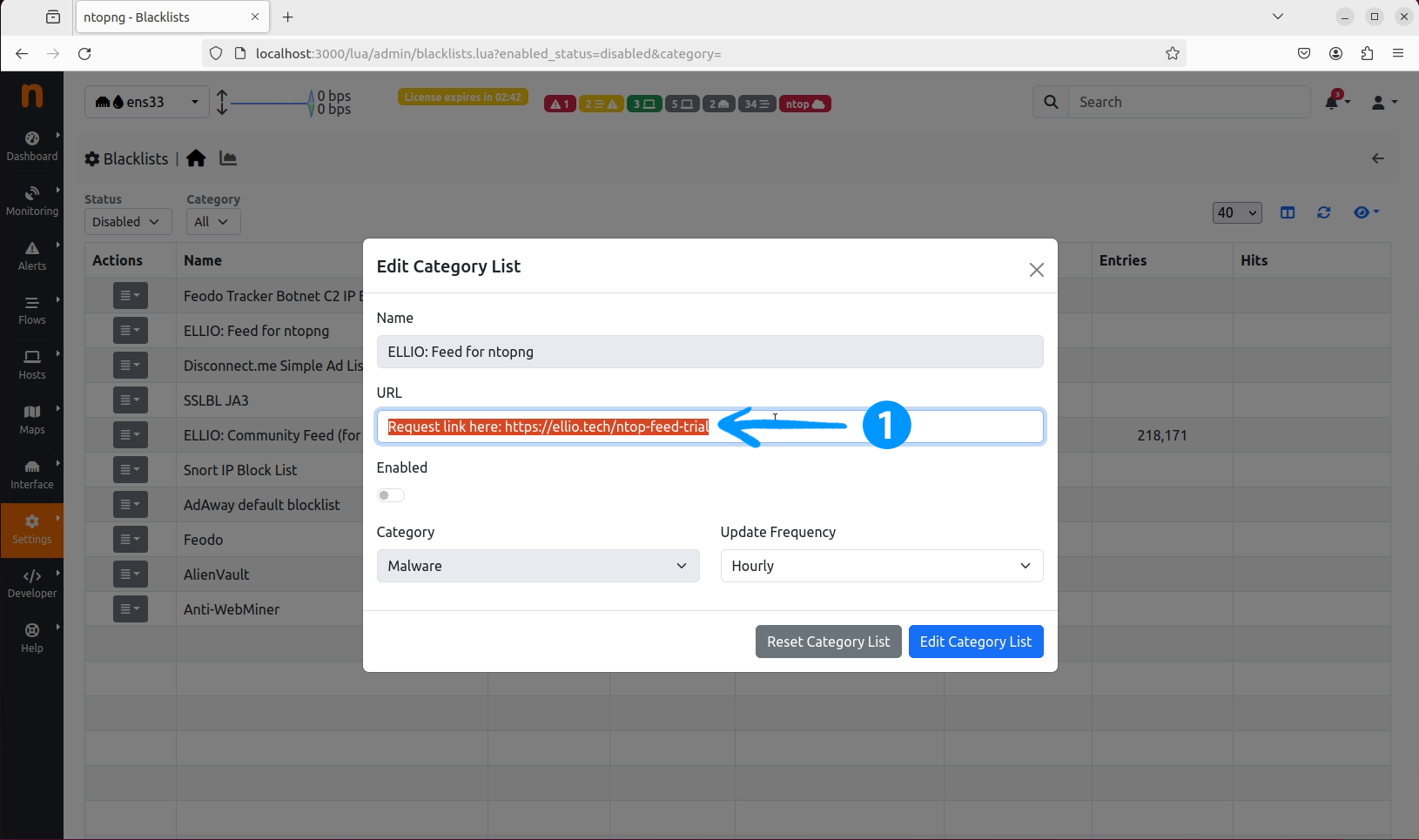
Edit Category List window, select the default Request link here... text in the URL field.
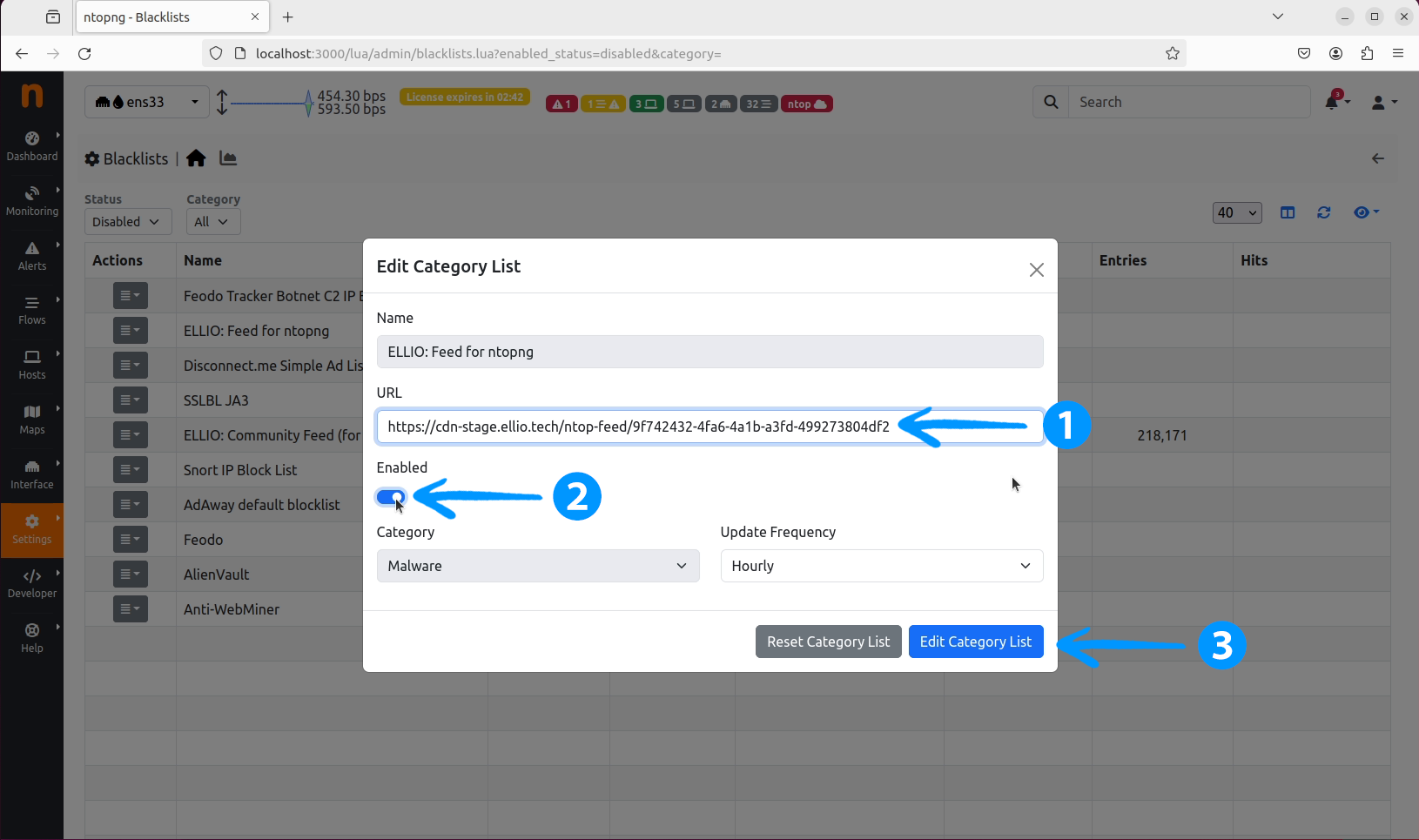
URL field, make sure it is Enabled and finally click on Edit Category List button, which will save your changes.
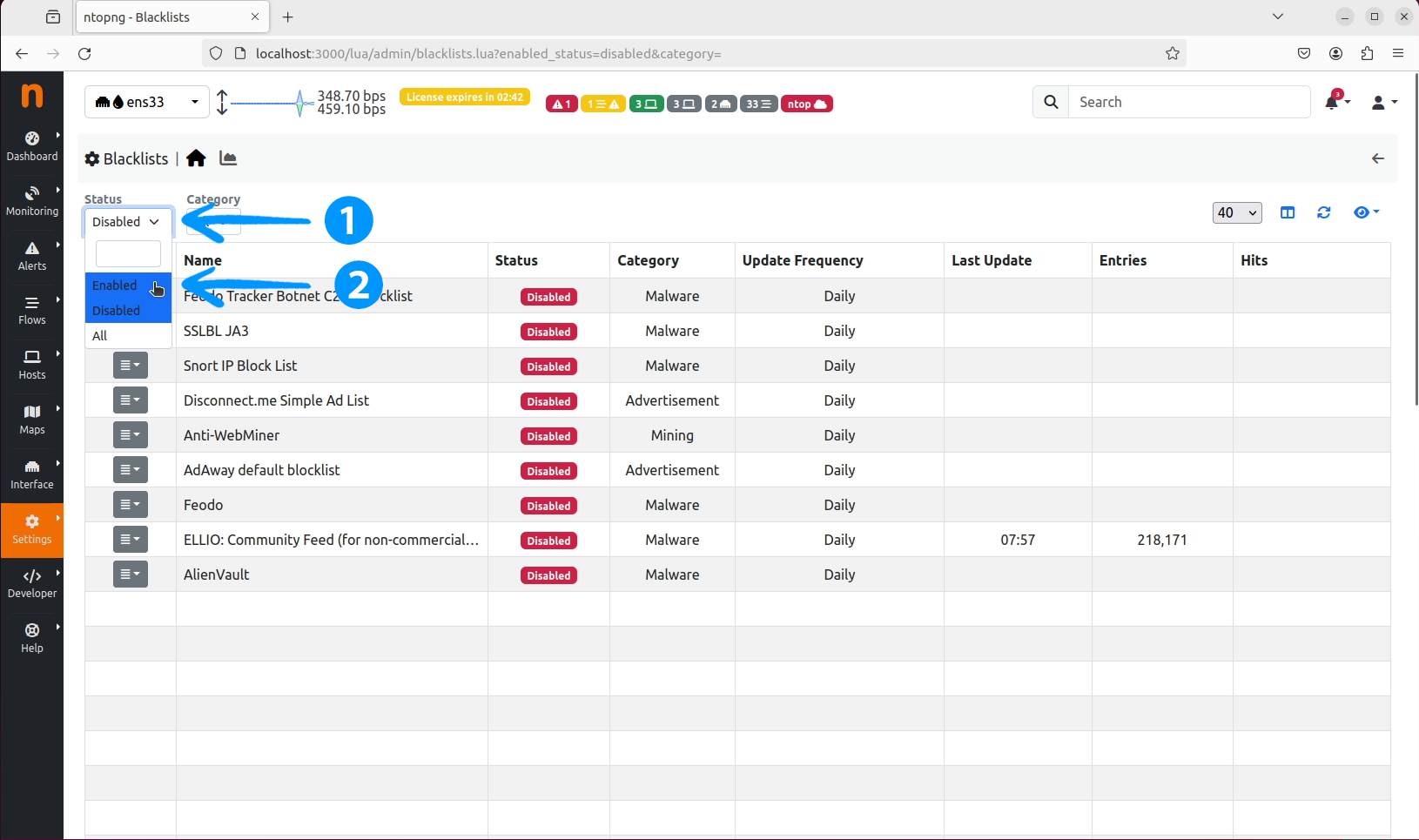
Status dropdown and select Enabled.
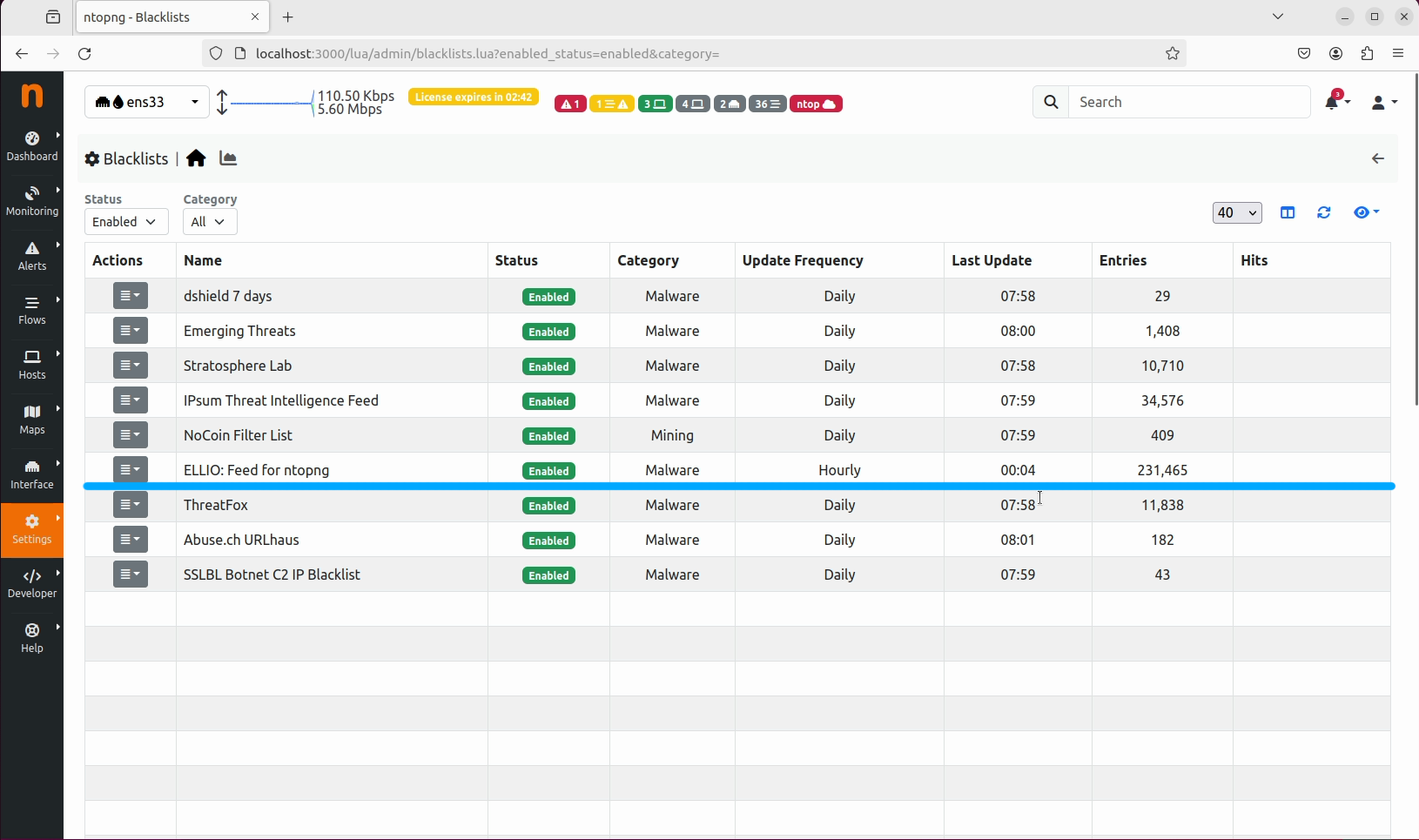
ELLIO: Threat List MAX for ntopng in the Blacklists section, with the status Enabled. Congratulations, you have successfully added ELLIO: Feed to your ntopng.
#
Adding ELLIO: Threat List MAX on stable build of ntopng
Go to /usr/share/ntopng/httpdocs/misc/lists/custom and add the ellio_tl_max.list file with the following content:
{"name":"ELLIO: Threat List MAX for ntopng,"format":"ip","enabled":true,"update_interval":3600,"url":"$YOUR_ELLIO_THREAT_LIST_MAX_URL","category":"malware"}$YOUR_ELLIO_THREAT_LIST_MAX_URL is the URL of your ELLIO: Threat List MAX. You should have received it in the email after the sign-up.
Once this part is done, go to the
#
Alerts
When ntopng triggers and alert for the flow based on the ELLIO: Threat List MAX, that means that actor observed by ELLIO doing malicious activities like opportunistic attacks, scans, mass exploitation or prey-and-spray attacks is trying to contact your network.
You can use that information to trigger an investigation, but it is advisable to use ELLIO: Threat List MAX filter out the traffic from the malicious actors by integrating the ELLIO: Threat List MAX with your firewall or router or inline mode nProbe™ Cento.
ELLIO: Threat List MAX is designed to be used for ingress traffic - that is the traffic that is coming into your network. The only exception is when you see your own IP addresses in the ELLIO: Threat List MAX - which means your infrastructure or your customers are engaging in malicious activities, and you can use that information to investigate and remediate the issue.
ntopng supports both scenarios.
If you need help with the best practices for alerting and investigation, threat hunting or ELLIO integration, please reach out to us here.
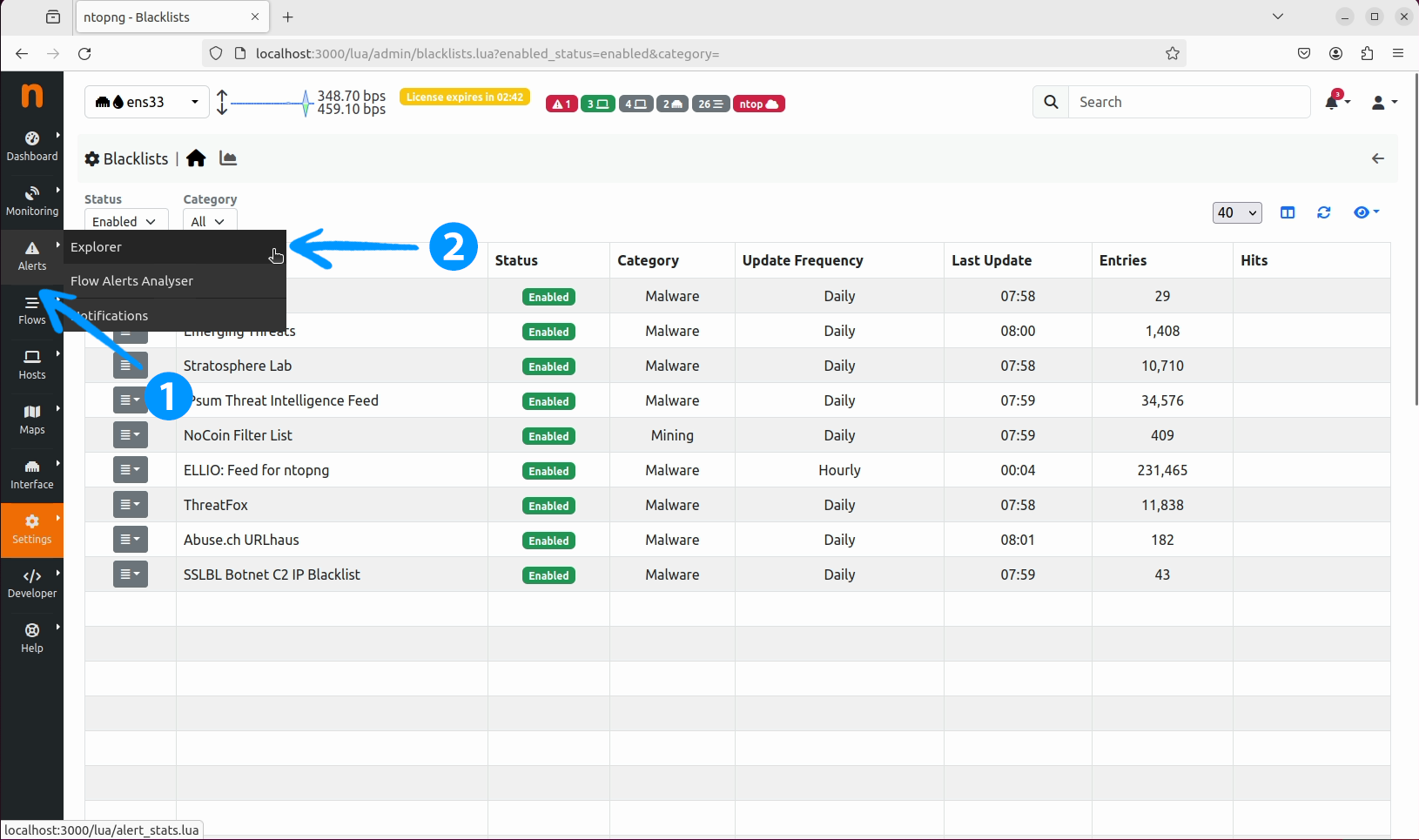
Alerts tab in the ntopng web interface and click on the Explorer button.
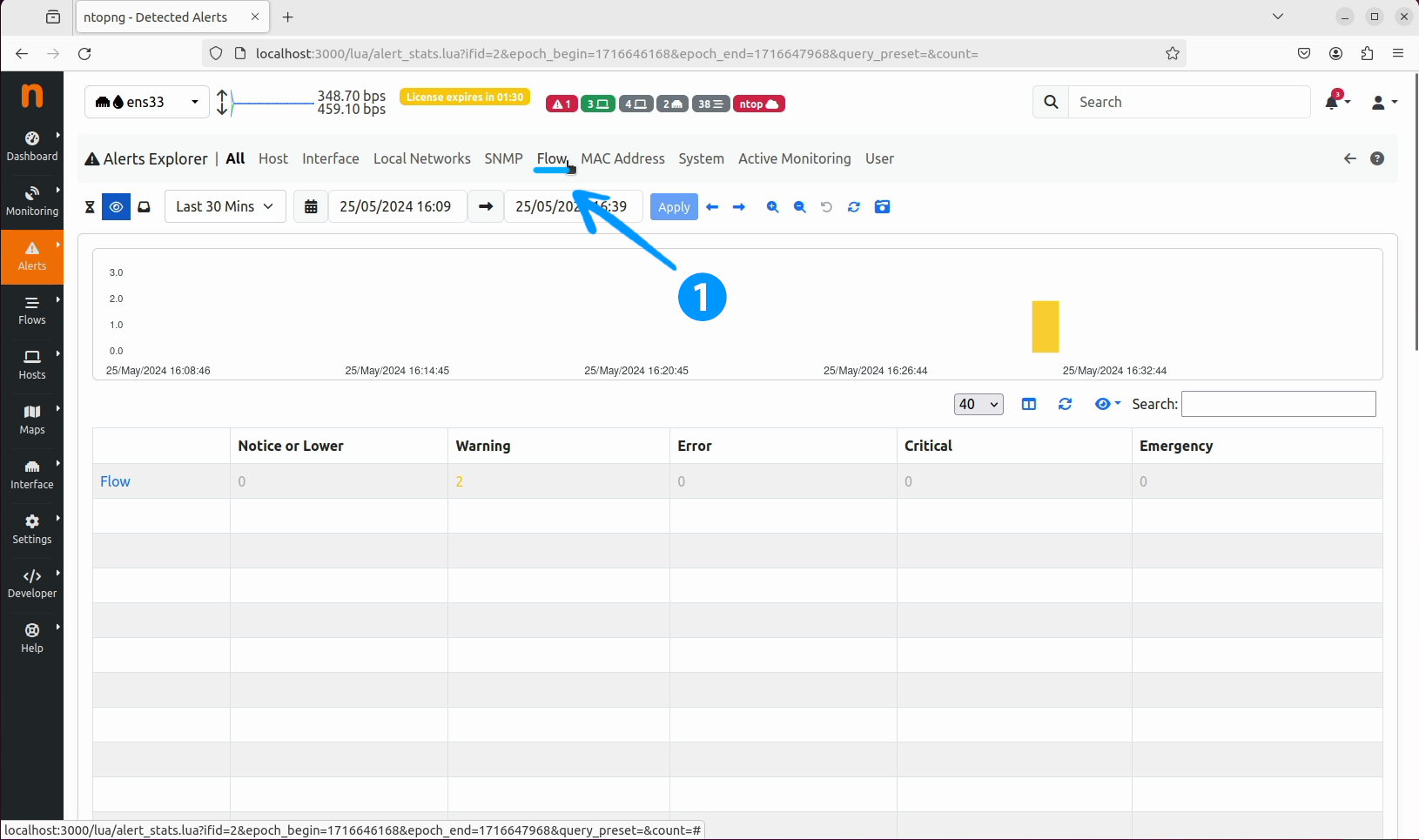
Explorer window, select the Flow tab.
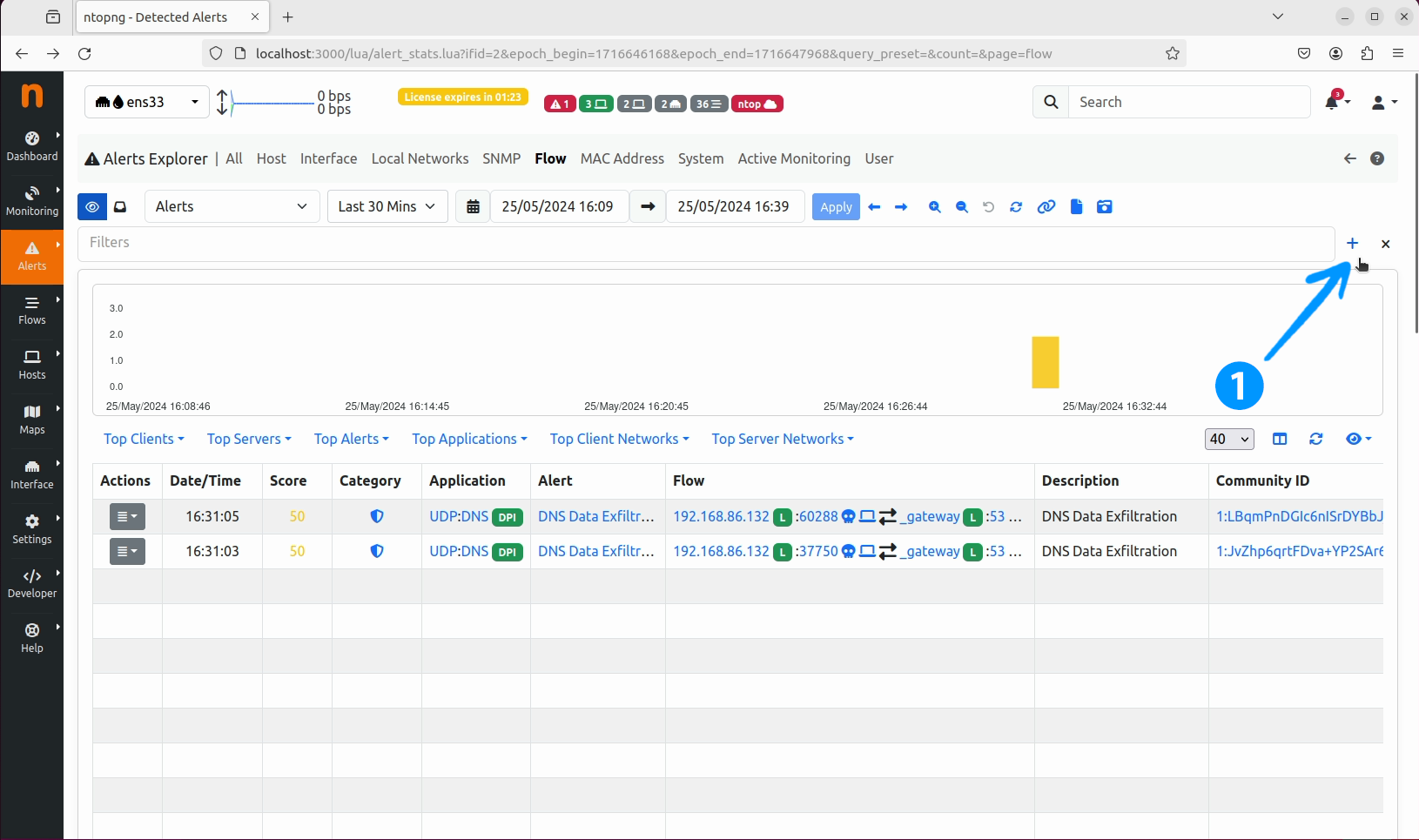
Flow tab, click on the + button to add a new filter.
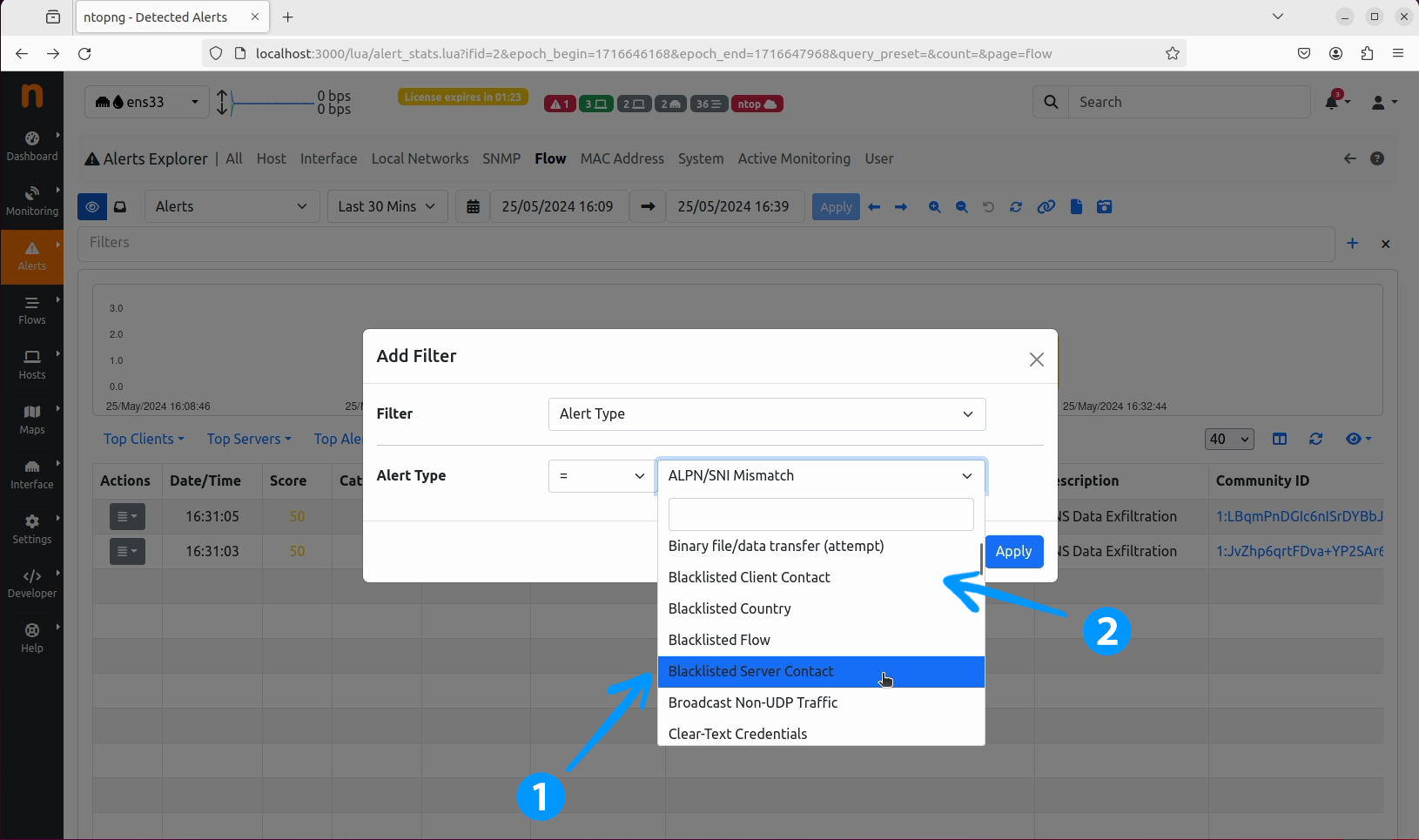
Add Filter window, select the Alert type dropdown and choose Blacklisted Server Contact from the list, to get the list of alerts from ELLIO: Threat List MAX for contacted hosts that are in ELLIO: Threat List MAX.
Alternatively, you can choose Blacklisted Client Contact to get the list of alerts with clients in ELLIO: Threat List MAX that were contacted .
#
Getting Help
If you need help with the best practices for alerting and investigation, threat hunting or ELLIO integration, please reach out to us here.